BPDU Guard
1. Introduction to BPDU Guard
What is BPDU Guard?
BPDU Guard is a security feature of the Spanning Tree Protocol (STP) designed to protect ports from receiving Bridge Protocol Data Units (BPDUs).
When a BPDU is detected on a BPDU Guard-enabled port, the port is immediately disabled (placed into an err-disable state) to prevent unauthorized or misconfigured devices from participating in the STP topology.
Let’s consider a scenario where BPDU Guard is not activated:
Before: Without BPDU Guard
If an unauthorized device is connected to a PortFast-enabled port and sends a BPDU with Bridge ID (BID): 4096:AABB.CCDD.EE10, it attempts to claim itself as the Root Bridge.

Interface G0/2 is configured as a PortFast interface which allows it to start forwarding traffic immediately. However, if a BPDU is received on this PortFast-enabled interface, it reverts to a regular STP port, potentially allowing an unauthorized device to disrupt the network topology.
After: Without BPDU Guard
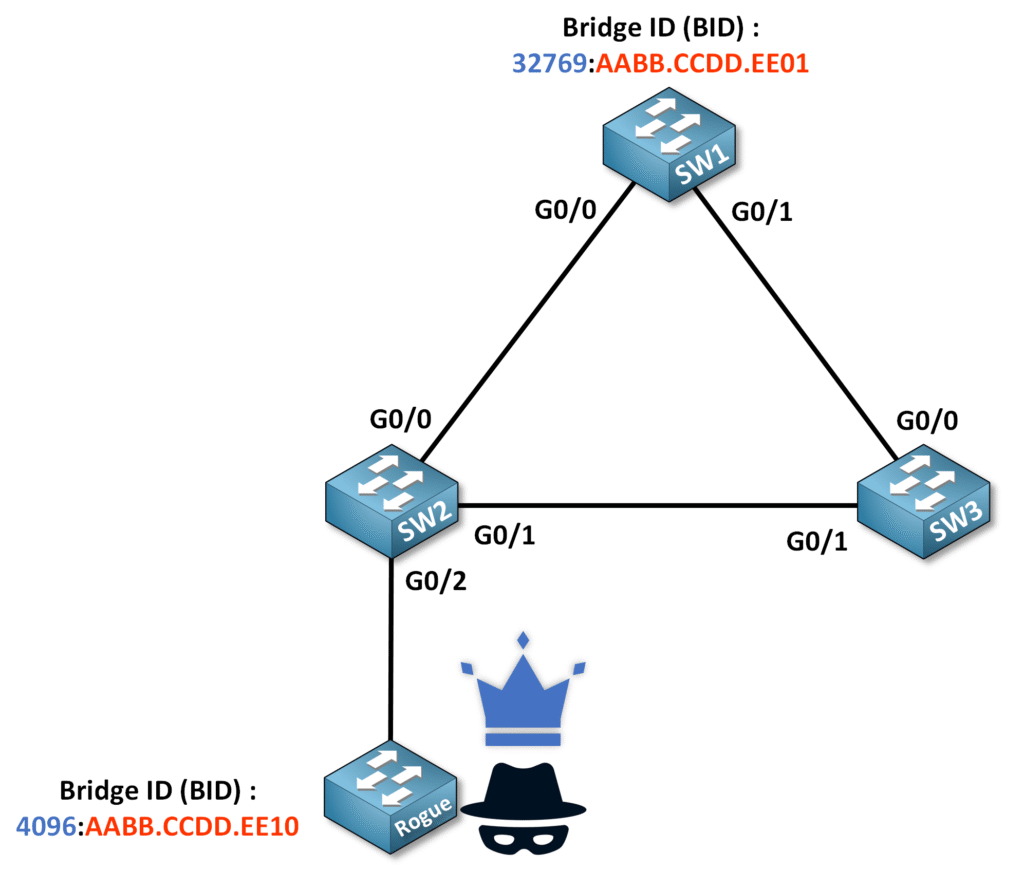
In this scenario, the unauthorized device successfully takes on the role of the Root Bridge by leveraging its superior priority value (4096).
This is a situation we must avoid in our network, as users could potentially connect their own switches to access ports and disrupt the network topology.
Solution: Enabling BPDU Guard
To prevent this situation, BPDU Guard is applied to the PortFast-enabled port. With BPDU Guard enabled, any incoming BPDU is immediately discarded and the port is placed into an err-disable state which brings the interface to the down/down state.
This ensures that PortFast-enabled ports, typically connected to end-user devices (PC) cannot receive BPDUs and modify the STP topology.
After: With BPDU Guard
Here is an example with BPDU Guard enabled on the interface connected to the rogue switch.
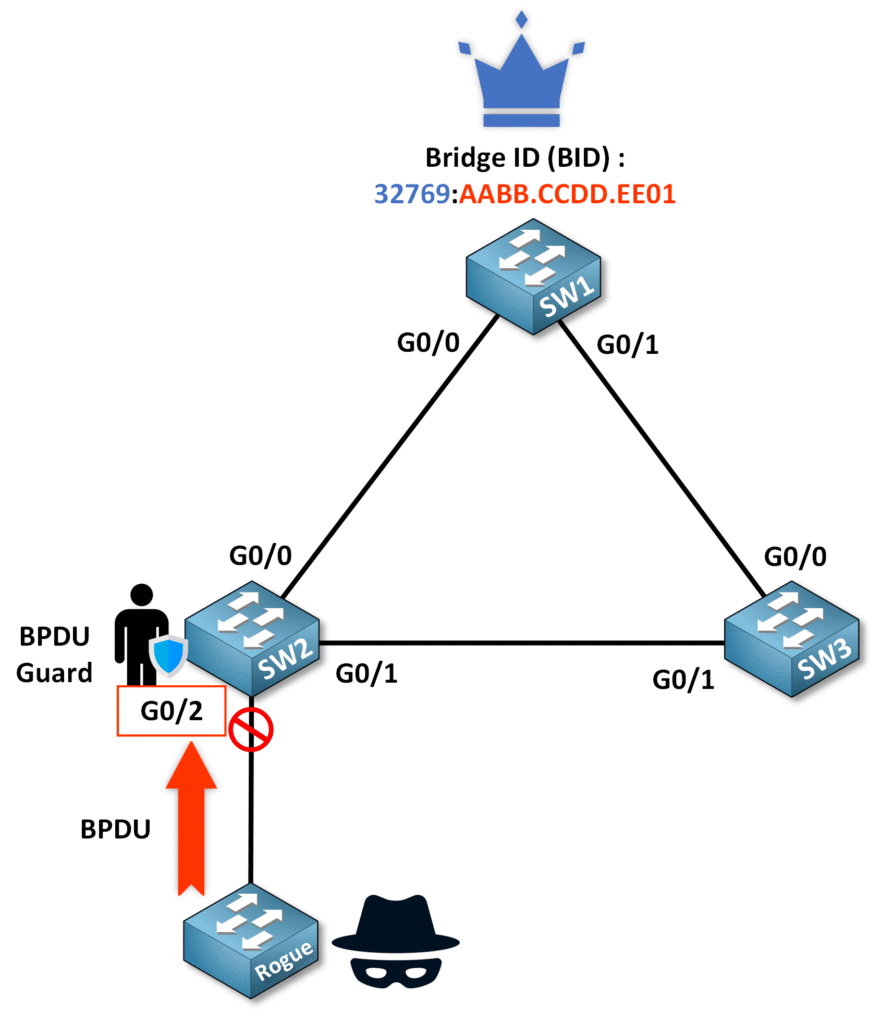
As shown in the output below, port G0/2 has been disabled by BPDU Guard, entered an err-disable state, and is now down.
*Dec 8 12:58:28.065: %SPANTREE-2-BLOCK_BPDUGUARD: Received BPDU on port Gi0/2 with BPDU Guard enabled. Disabling port.
*Dec 8 12:58:28.066: %PM-4-ERR_DISABLE: bpduguard error detected on Gi0/2, putting Gi0/2 in err-disable state
*Dec 8 12:58:29.073: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to down
*Dec 8 12:58:30.109: %LINK-3-UPDOWN: Interface GigabitEthernet0/2, changed state to down
Now, let’s dive into the configuration steps together—it’s simpler than you think !
2. Configuring BPDU Guard
Pre-Configuration Checklist
Before enabling BPDU Guard, it’s important to understand that BPDU Guard and PortFast are separate features. While they are often used together, they can be configured independently based on your network requirements.
If your goal is to enable instant forwarding state for end hosts (PCs, printers) and protect the port from receiving unauthorized BPDUs, you should configure both PortFast and BPDU Guard on the same port.
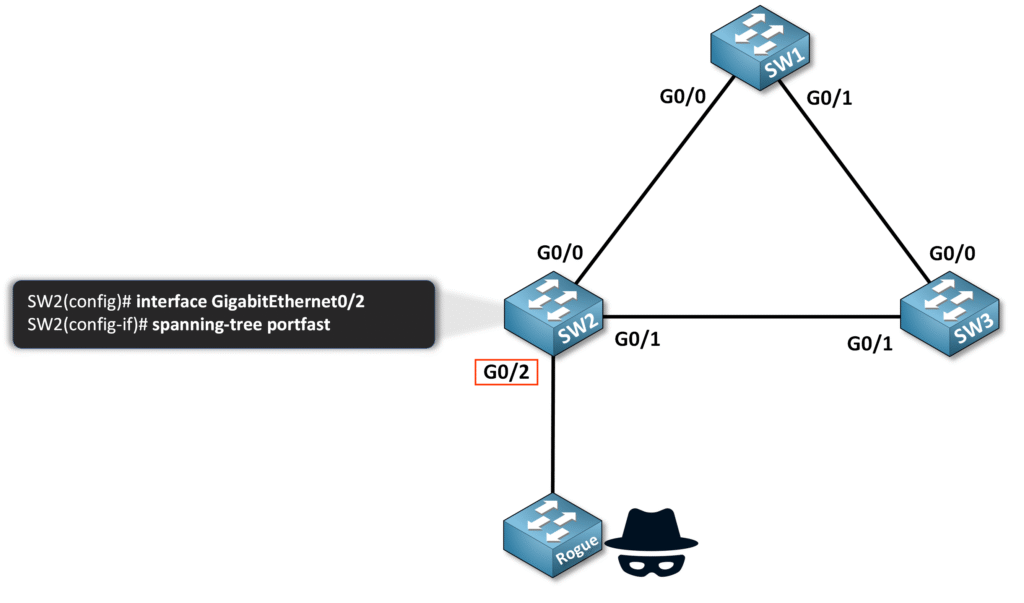
In this example, we will configure PortFast to achieve rapid forwarding for end hosts and add BPDU Guard for protection features against rogue BPDUs on interface G0/2 of switch SW2.
BPDU Guard can be configured in two ways:
- On Individual Ports: Applied specifically to selected interfaces
- Globally: Automatically applied to all PortFast-enabled ports
Enabling BPDU Guard on Individual Ports
Configuration Steps:
- Enter interface configuration mode:
SW2(config)# interface GigabitEthernet0/2
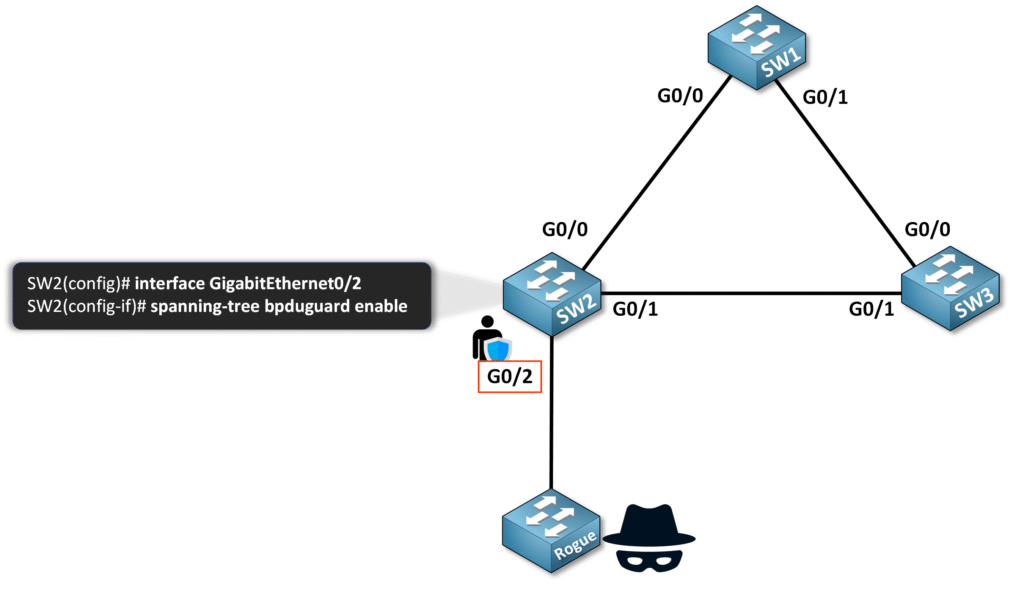
2. Enable BPDU Guard on the interface:
SW2(config-if)# spanning-tree bpduguard enable
Checking BPDU Guard Status
To confirm BPDU Guard is enabled and functioning, use the following verification commands:
SW2(config-if)# show spanning-tree interface g0/2 detail
Port 3 (GigabitEthernet0/2) of VLAN0001 is designated forwarding
Port path cost 4, Port priority 128, Port Identifier 128.3.
Designated root has priority 32769, address 50e2.aa04.6b00
Designated bridge has priority 32769, address 50e2.aa04.6b00
Designated port id is 128.3, designated path cost 0
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
The port is in the portfast edge mode
Link type is point-to-point by default
Bpdu guard is enabled
BPDU: sent 3, received 0
As you can see in the output, BPDU guard is enabled !
This configuration ensures that if BPDUs are received on this port, it will immediately shut down and place into Err-disable state.
Verify BPDU Guard
Since interface G0/2 is configured with BPDU Guard, it is protected against rogue switches sending BPDUs.
If a BPDU is detected, the interface will transition to an err-disabled state and shut down, as confirmed in the CLI output.

SW2# show interfaces g0/2 GigabitEthernet0/2 is down, line protocol is down (err-disabled) !output omitted
With this configuration, the port is now protected against unauthorized devices attempting to disrupt the network by sending BPDUs.
Disabling BPDU Guard on Individual Ports
There is also a command available to disable BPDU Guard on individual ports if needed.

SW2(config)# int g0/2 SW2(config-if)# spanning-tree bpduguard disable
Enabling BPDU Guard Globally
BPDU Guard can also be enabled globally, applying it automatically to all PortFast-configured ports on the switch.
SW2(config)# spanning-tree portfast bpduguard default
3. Understanding ErrDisable State
What is ErrDisable?
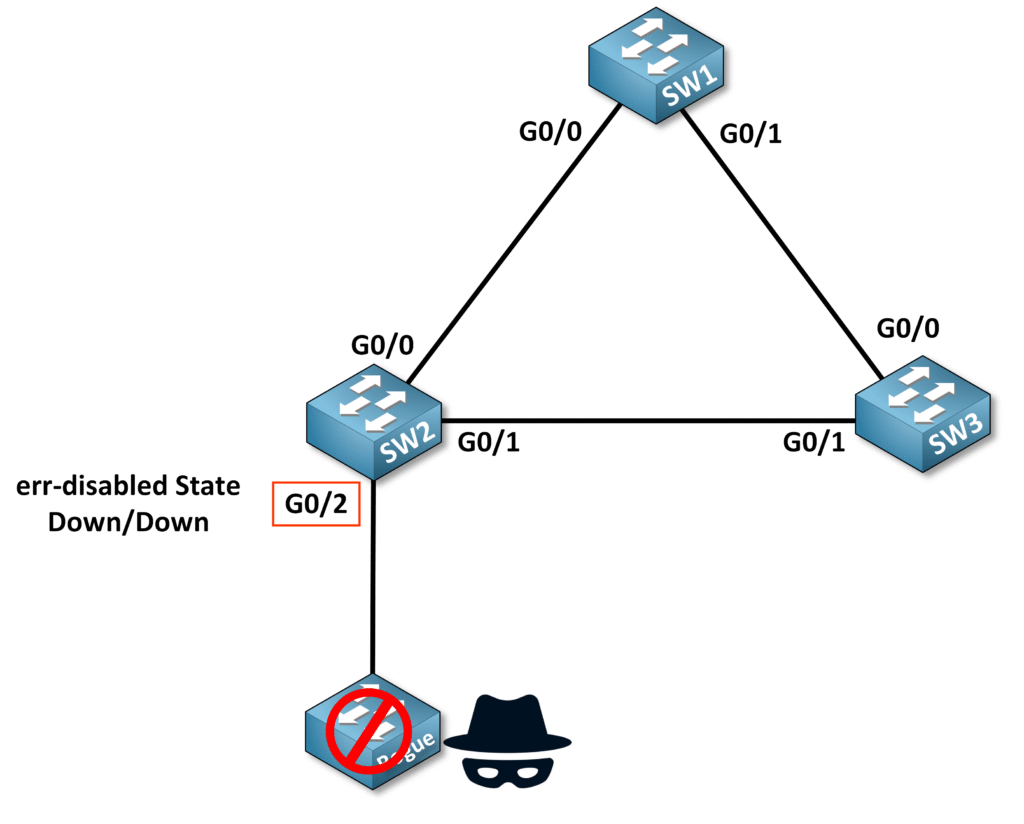
The ErrDisable mechanism is used by BPDU Guard to disable a port (state: down/down) and place it in an err-disabled state to prevent potential network disruptions.
When BPDU Guard detects an unwanted BPDU, it blocks the port and transitions it to the err-disabled state, as shown in the example below:
Before re-enabling an err-disabled port, it is crucial to ensure that the unauthorized device responsible for sending the BPDU has been removed from the network.
4. Recovering Ports from ErrDisable State
There are two methods to bring an err-disabled port back into an operational state:
- Manual Recovery: Use the
shutdownandno shutdowncommands to manually reset the port. - Automatic Recovery: Use the ErrDisable Recovery Mechanism to automatically re-enable the port after a specific timeout period.
Manual Recovery
To recover a port manually:
- Shutdown and No Shutdown the interface:
SW2(config)# interface g0/2 SW2(config-if)# shutdown SW2(config-if)# no shutdown
2. Re-enable the interface:
SW2# show interfaces g0/2 GigabitEthernet0/2 is up, line protocol is up (connected) !output omitted
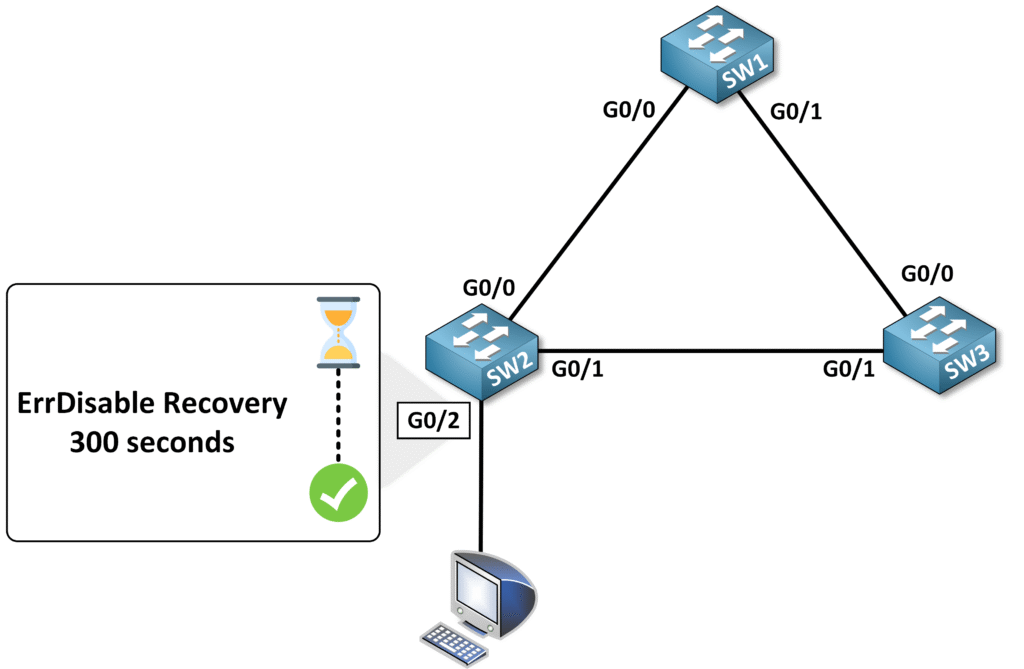
Automatic Recovery with ErrDisable Recovery
There is also an automatic way to recover from the ErrDisable state using the ErrDisable Recovery Mechanism.
By default, this mechanism is disabled. You can check its current status with the following command:
SW2# show errdisable recovery
ErrDisable Reason Timer Status
----------------- --------------
arp-inspection Disabled
bpduguard Disabled
!output omitted
Timer interval: 300 seconds
Interfaces that will be enabled at the next timeout:
Enabling Automatic Recovery
To enable ErrDisable Recovery for a specific cause, such as BPDU Guard:
SW2(config)# errdisable recovery cause bpduguard
Verify that ErrDisable Recovery has been enabled:
SW2# show errdisable recovery
ErrDisable Reason Timer Status
----------------- --------------
arp-inspection Disabled
bpduguard Enabled
!output omitted
Timer interval: 300 seconds
Interfaces that will be enabled at the next timeout:
Interface Errdisable reason Time left(sec)
--------- ----------------- --------------
Gi0/2 bpduguard 299
In this example, Gi0/2 is scheduled to recover in 299 seconds.
Recovery in Action
Once the timer expires, the port is automatically restored to the up/up state. The following logs illustrate the recovery process:
*Dec 8 15:30:45.261: %PM-4-ERR_RECOVER: Attempting to recover from bpduguard err-disable state on Gi0/2 *Dec 8 15:30:47.290: %LINK-3-UPDOWN: Interface GigabitEthernet0/2, changed state to up *Dec 8 15:30:48.290: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to up
Customizing the Recovery Timer
The default recovery timer is 300 seconds, but it can be customized to fit your network needs.
- View the available timer range:
SW2(config)# errdisable recovery interval ? <30-86400> timer-interval(sec)
2. Set a custom timer (Example 30 seconds):
SW2(config)# errdisable recovery interval 30
5. Conclusion
BPDU Guard is a vital feature to secure PortFast-enabled ports, protecting your network from unauthorized devices and ensuring stability. Here’s what you’ve learned:
- What is BPDU Guard?
- Disables a port (err-disabled state) if it receives a BPDU, preventing rogue devices from disrupting the STP topology.
- Disables a port (err-disabled state) if it receives a BPDU, preventing rogue devices from disrupting the STP topology.
- Configuration
- Enable BPDU Guard on individual ports or globally for all PortFast-enabled ports. Ensure PortFast is active first.
- Enable BPDU Guard on individual ports or globally for all PortFast-enabled ports. Ensure PortFast is active first.
- ErrDisable State
- Ports are disabled to block unauthorized devices. Always remove the rogue device before recovering the port.
- Ports are disabled to block unauthorized devices. Always remove the rogue device before recovering the port.
- Port Recovery
- Manual: Use
shutdownandno shutdown. - Automatic: Enable ErrDisable Recovery for automatic reactivation after a timeout.
- Manual: Use
By leveraging BPDU Guard, you ensure your network remains stable and secure against unauthorized devices.
