FTP and TFTP
1. Introduction to FTP and TFTP
Overview
🔍 File Transfer Protocol (FTP) and Trivial File Transfer Protocol (TFTP) are two key protocols in network management. These protocols enable the transfer of files between devices, which is critical for tasks like configuration updates, software patches, and backup processes. While FTP includes a basic authentication system, it does not provide encryption, making it less secure on its own. TFTP, on the other hand, offers a simpler, faster method for quick file exchanges without authentication.
💡 Real-world example: A network administrator uses FTP to back up configuration files to a server, ensuring they can restore them if issues arise.

Importance in Network Management
🛠️ FTP and TFTP are essential for day-to-day network management tasks:
✅ Configuration backups: Store configurations to restore devices quickly in case of failure.
✅ Software updates: Transfer firmware or software updates to devices.
✅ Disaster recovery: Quickly restore devices using saved configurations or software.
Port Numbers and Protocols
FTP and TFTP use specific port numbers that are important for configuration and network security:
- FTP uses TCP port 21 for control and TCP port 20 for data transfers, which is essential to remember for firewall configurations.

- TFTP uses UDP port 69, making it faster but less reliable than FTP due to the lack of connection-based communication.

2. Understanding FTP (File Transfer Protocol)
What is FTP?
🔍 FTP is a protocol that allows files to be transferred over a network using Transmission Control Protocol (TCP). It’s reliable and supports two modes—active and passive—for handling data flow between the client and server. FTP is commonly used for file transfers that require basic authentication but lacks built-in encryption, so it should not be considered fully secure on its own.
💡 Example: A network engineer uploads router configurations to an FTP server for centralized backup.
FTP Modes
FTP operates in two main modes: Active Mode and Passive Mode, each using different methods for control and data transfer.
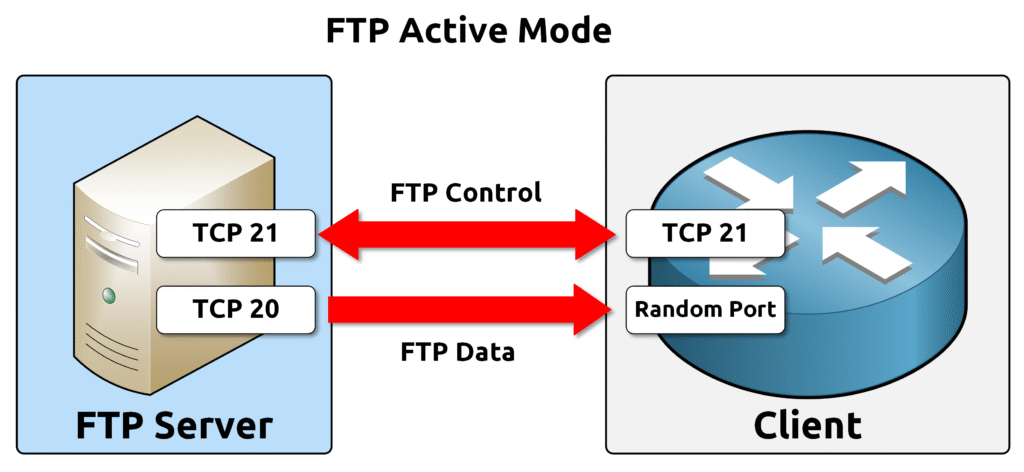
Active Mode
🔍 In Active Mode, the client connects to the server’s control port (TCP 21) and specifies a port on the client side to listen for incoming data. The server then initiates the data connection from its data port (TCP 20) to the client’s designated port.
⚠️ This mode can cause issues with firewalls because the server initiates the data connection, which might be blocked as an unsolicited incoming request.
Passive Mode
🔍 In Passive Mode, the client also connects to the server’s control port (TCP 21) but avoids server-initiated data connections. Instead, the server opens a random port and communicates this to the client. The client then initiates the data connection to that port.
✅ Passive Mode is generally preferred because it is more compatible with firewalls, as all connections are client-initiated.

Uploading and Downloading Files with FTP
✅ Uploading Files: Uploading is the process of sending files from the client to the FTP server. For example, a network engineer may upload router configuration files from their computer to a centralized FTP server. This practice is essential for creating backups and managing configurations in a centralized location.
✅ Downloading Files: Downloading is retrieving files from the FTP server to the client. This is often done to restore a previous configuration or install firmware on a network device. For instance, a technician might download a backed-up configuration file from the FTP server to a router after a factory reset.
FTP Security Considerations
Common Vulnerabilities
⚠️ FTP lacks encryption, meaning all data, including usernames and passwords, is transmitted in plain text. This creates significant vulnerabilities, especially when FTP traffic is exposed on a public network. Potential attackers could intercept sensitive information, making FTP insecure for transferring confidential data without additional security measures.
Securing FTP Transfers with FTPS and SFTP
✅ While traditional FTP lacks security, two secure alternatives can be mentioned:
- FTPS (FTP Secure): FTPS adds SSL/TLS encryption to FTP, securing the data transfer process and protecting credentials. This allows organizations to use FTP securely by preventing unauthorized access to sensitive data in transit.
- SFTP (SSH File Transfer Protocol): SFTP is a different protocol that uses SSH (Secure Shell) to encrypt data, offering robust security for transferring files. Unlike FTPS, SFTP uses a single connection (usually on TCP port 22), making it easier to configure with firewalls.
📢 In the next section, we’ll explore TFTP, its key differences from FTP, and common use cases.
3. Understanding TFTP (Trivial File Transfer Protocol)
🔍 What is TFTP?
Trivial File Transfer Protocol (TFTP) is a simplified file transfer protocol designed for basic, rapid file exchanges. It uses UDP (User Datagram Protocol) instead of TCP, making it faster but less reliable. TFTP lacks built-in security features like authentication and encryption, so it’s primarily used for simple, low-risk tasks within secure environments.
💡 Example: TFTP is often used to load configuration files or firmware onto routers and switches during boot, streamlining the setup process without manual configuration.
🔍 Key Differences Between FTP and TFTP
- FTP: Utilizes TCP (Transmission Control Protocol), supports authentication, and is more suitable for controlled, secure transfers.
- TFTP: Operates over UDP (User Datagram Protocol), does not provide authentication, and is ideal for quick, straightforward file transfers where security is not a concern.
🔍 Common Use Cases for TFTP
✅ Device Bootstrapping: TFTP is commonly used to load initial configurations onto devices like routers and switches during boot, helping them get online quickly.
✅ Firmware Updates: Administrators often use TFTP for rapid firmware updates, especially in lab environments or secure internal networks.
✅ Network Labs and Testing: TFTP is ideal for environments where devices need frequent resets or configuration changes, as it allows quick, repeated file transfers without security overhead.
⚠️ Warning: Due to its lack of security, TFTP should not be used to transfer sensitive data. It is best suited for secure, controlled environments where speed and simplicity are prioritized over security.
4. Configuring FTP on Cisco Devices
🛠️ Prerequisites
This topology will be used to configure FTP:

- FTP Server: IP
192.168.1.10– stores the configuration backups. - Cisco Router (R1): IP
192.168.1.1– the device that will back up its configuration to the FTP server.
🔍 Step-by-Step FTP Configuration on Cisco Router
🔹 Step 1: Configure the FTP Source Interface
Enter global configuration mode:
R1# configure terminal
Specify the source interface for FTP traffic (use the interface connected to the FTP server’s subnet):
R1(config)# ip ftp source-interface GigabitEthernet0/0
🔹 Step 2: Set FTP Username and Password
Define the FTP username and password:
R1(config)# ip ftp username cisco R1(config)# ip ftp password cisco123
Exit configuration mode:
R1(config)# end
🔹 Step 3: Verify Connectivity to the FTP Server
Test connectivity to the FTP server:
R1# ping 192.168.1.10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/3 ms
✅ A successful ping confirms network reachability to the FTP server.
🔹 Step 4: Backup Running Configuration to FTP Server
Initiate the backup of the running configuration:
R1# copy running-config ftp: Address or name of remote host []? 192.168.1.10 Destination filename [R1-confg]? R1-Backup Writing running-config... [OK - 625 bytes] 625 bytes copied in 0.030 secs (20833 bytes/sec)
When prompted, specify the FTP server’s IP address (in this case, 192.168.1.10) as the remote host. For the destination filename, you can provide a custom name (e.g., R1-Backup) to save the backup file on the FTP server. This confirms that the running configuration was successfully backed up !
