Port Security
1. Introduction to Port Security
Port Security Features
By default, all Cisco switch interfaces are enabled meaning any device with physical access can connect to the network.

While this is convenient, it poses a significant security risk, especially in offices, public spaces, or other environments where unauthorized users could plug in their devices.
Without restrictions, the switch would accept the connection, potentially enabling unauthorized access or even malicious attacks.

To mitigate this risk, we use Port Security.
Port Security allows administrators to control and restrict access to switch ports based on MAC addresses.
- What does this mean?
A switch port can be configured to allow only specific devices based on their MAC addresses. - What happens if an unauthorized device connects?
The switch blocks the connection, preventing unauthorized access, as shown in the illustration above.
How Port Security Works
Port Security is a Layer 2 security feature that validates the source MAC addresses of devices connecting to a switch port.

It enables administrators to precisely define which devices can access specific ports by using MAC Address.
2. Configuring Port Security
Before securing a switch port, we must ensure it knows which MAC addresses are trusted.
Switches can learn MAC addresses dynamically or be configured with static assignments. Let’s explore the different techniques used to learn trusted MAC addresses.
Dynamic Learning (Default)
The first method is Dynamic Learning, which is the default behavior.
- We enable Port Security on the interface.
- The legitimate device is connected and sends traffic through the port.
- The switch dynamically learns the MAC address and considers it trusted.

By default, only one MAC address is allowed per port. If another device attempts to connect and send traffic, it will be denied access.
Static Configuration
The next approach is to manually define the trusted MAC address.
For example, if we have a device with MAC address AAAA.BBBB.CCCC, we can statically configure the switch port to only accept frames from this MAC address.

While this method provides strict security, it can be time-consuming, especially when managing multiple interfaces.
Number of Allowed MAC Addresses
By default, **only 1 MAC address is permitted per portµµ.
However, in cases where multiple devices share a port (PC and an IP phone connected to a switch), we can modify the maximum number of allowed MAC addresses.

In this example, the switch is configured to dynamically learn and allow 2 MAC addresses on the same port.
Alright, that covers the basics! Now, let’s get technical and configure Port Security with its default settings to see it in action.
3. Port Security Default Configuration
Now, let’s see what happens when we enable Port Security using default settings and how the switch reacts when an unauthorized device tries to connect.
Understanding the Default Behavior
Imagine a simple setup where PC1 is connected to SW1.

By default, when Port Security is enabled on a switch interface, the following happens:
✅ The switch learns the first MAC address that sends traffic.
✅ This MAC address is considered trusted.
🚫 Any additional MAC address attempting to send traffic on the same port triggers a security violation.
Now, let’s configure Port Security and observe its behavior.
Configuring Port Security
Let’s enable Port Security on interface g0/1 using the following command:
SW1(config)# int g0/1
SW1(config-if)# switchport port-security
Command rejected: GigabitEthernet0/1 is a dynamic port.
Wait, what happened?
The command was rejected because the interface is in dynamic auto mode, which does not support Port Security.
Fixing the Interface Mode
To enable Port Security, the port must be in access mode or trunk mode. Let’s check the current mode:
SW1# show interfaces g0/1 switchport Name: Gi0/1 Switchport: Enabled Administrative Mode: dynamic auto Operational Mode: static access !!! Output omitted !!!
Since the administrative mode is dynamic auto, we need to manually set it to access mode before enabling Port Security:
SW1(config)# int g0/1 SW1(config-if)# switchport mode access
Now, we can successfully enable Port Security:
SW1(config-if)# switchport port-security
Verifying Port Security Configuration
To check the current Port Security settings on g0/1, use:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 0 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0000.0000.0000:0 Security Violation Count : 0
Breakdown of the Output:
- ✅ Port Security: Enabled
- ✅ Port Status:
Secure-up(port is active) - ✅ Violation Mode:
Shutdown(default action for unauthorized devices) - ✅ Maximum MAC Addresses:
1(default) - ❌ Total MAC Addresses:
0(the port hasn’t learned any MAC addresses yet)
Since no traffic has passed through the port yet, the last source address remains empty.
When Traffic is Detected
Once PC1 sends traffic, the switch dynamically learns its MAC address.

Now, if we check the port security status again:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : AAAA.BBBB.CCCC:1 Security Violation Count : 0
What Changed?
- The Total MAC Addresses has increased from
0to1→ The switch learned PC1’s MAC address (AAAA.BBBB.CCCC). - The Last Source Address is now PC1’s MAC, confirming that it was successfully recorded.
Since the port only allows one MAC address, any additional device will trigger a security violation.
What Happens When an Unauthorized Device Connects?
Now, let’s say a hacker plugs in a second device to the same port.
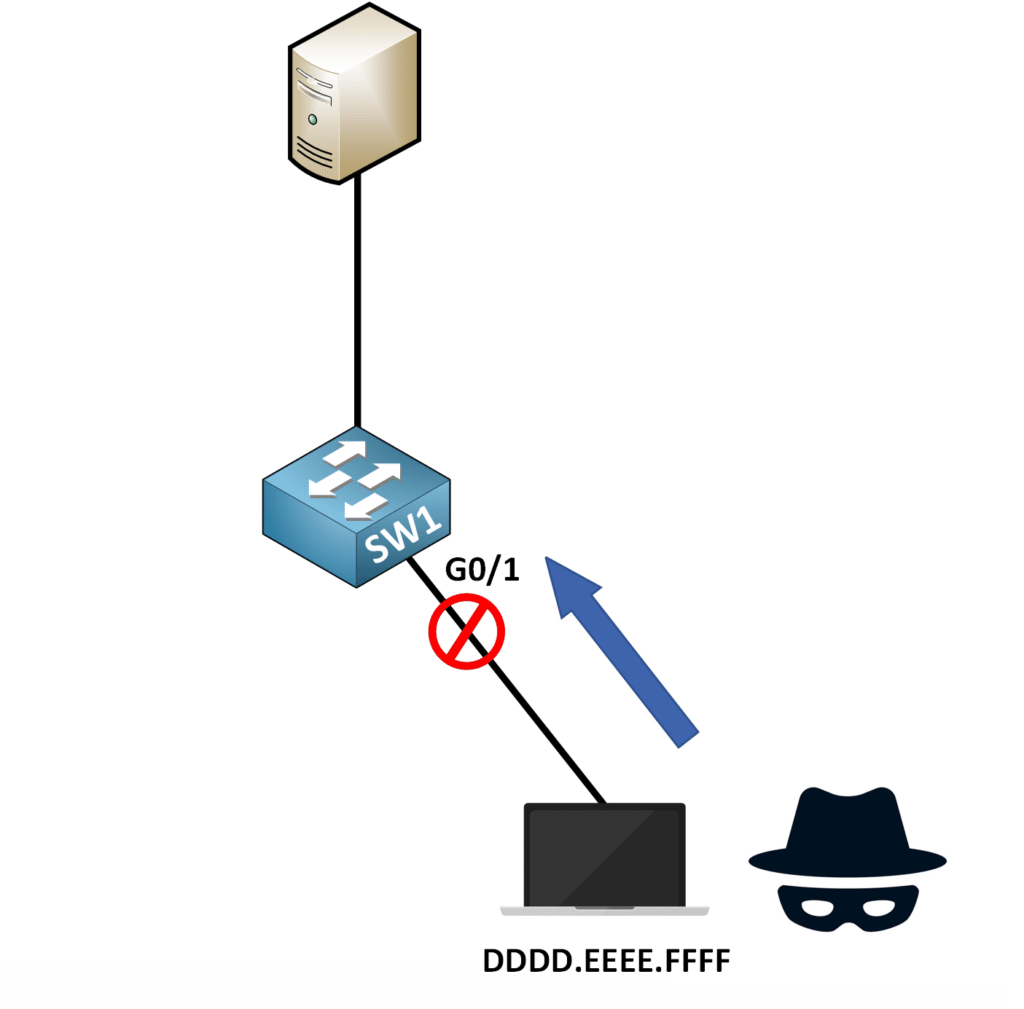
The hacker’s MAC address (DDDD.EEEE.FFFF) is different from PC1’s MAC (AAAA.BBBB.CCCC). The switch detects a security violation and takes action.
Logs of the Security Violation
*Jan 21 11:21:46.891: %PM-4-ERR_DISABLE: psecure-violation error detected o n Gi0/1, putting Gi0/1 in err-disable state *Jan 21 11:21:46.894: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violatio n occurred, caused by MAC address DDDD.EEEE.FFFF on port GigabitEthernet0/1 *Jan 21 11:21:48.893: %LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to down
✅ The port is now disabled (err-disabled state), preventing any further unauthorized traffic.
Checking the Port Security Status
To investigate, we run:
SW1#show port-security interface g0/1
Port Security : Enabled
Port Status : Secure-shutdown
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 0
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : DDDD.EEEE.FFFF:1
Security Violation Count : 1
Here’s what we see:
- ⚠ Port Status:
Secure-shutdown→ The port has been disabled. - 🚨 Last Source Address: The hacker’s MAC address (
DDDD.EEEE.FFFF). - 🔴 Security Violation Count:
1, meaning the switch has registered one unauthorized connection attempt.
Verifying the Interface Status
To confirm the port is disabled, we can check its status:
SW1# show interfaces status
Port Name Status Vlan Duplex Speed Type
Gi0/0 connected 1 auto auto RJ45
Gi0/1 err-disabled 1 auto auto RJ45
The port status is now err-disabled, confirming that no traffic is allowed through this interface until the issue is resolved.
Now that the interface is err-disabled due to a security violation, how do we recover it?
4. Re-Enable Interface
When an interface enters the err-disabled state due to a security violation, there are two ways to bring it back to normal operation:
- Manual Recovery – Requires administrative intervention.
- Automatic Recovery (Err-Disable Recovery) – Enables the switch to automatically recover the interface after a set timeout.
Manually Re-Enabling the Interface
The manual method requires an administrator to reset the interface. However, before proceeding, you must disconnect the unauthorized device that caused the security violation. If the device remains connected, the interface will re-enter the err-disabled state as soon as it detects traffic from the untrusted MAC address.
Steps for Manual Recovery
Once the unauthorized device is removed, follow these steps to manually reset the interface:
SW1(config)# int g0/1 SW1(config-if)# shutdown SW1(config-if)# no shutdown
- The
shutdowncommand administratively disables the interface. - The
no shutdowncommand reactivates the interface.
Now, verify the port security status:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 0 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0000.0000.0000:0£ Security Violation Count : 0
What’s changed?
- ✅ The port status is now
Secure-up(active again). - ✅ The last source address (hacker’s MAC) has been cleared.
- ✅ The security violation count is reset to
0.
While this method works well, it requires manual intervention each time a violation occurs. In large networks, this can be impractical. That’s where automatic recovery comes in.
Err-Disable Recovery
Err-Disable Recovery allows the switch to automatically re-enable err-disabled interfaces after a set timeout, eliminating the need for manual intervention.
Checking the Current Err-Disable Recovery Configuration
This method use a feature that enable to be automatically re-enabled an err-disabled interfaces after a certain period of time !
By default, Err-Disable Recovery is disabled for all error causes, including psecure-violation (port security violation). To check its status, use:
SW1# show errdisable recovery ErrDisable Reason Timer Status ----------------- -------------- arp-inspection Disabled bpduguard Disabled channel-misconfig (STP) Disabled dhcp-rate-limit Disabled dtp-flap Disabled gbic-invalid Disabled inline-power Disabled l2ptguard Disabled link-flap Disabled mac-limit Disabled link-monitor-failure Disabled loopback Disabled oam-remote-failure Disabled pagp-flap Disabled port-mode-failure Disabled pppoe-ia-rate-limit Disabled psecure-violation Disabled security-violation Disabled sfp-config-mismatch Disabled storm-control Disabled udld Disabled unicast-flood Disabled vmps Disabled psp Disabled dual-active-recovery Disabled evc-lite input mapping fa Disabled Recovery command: "clear Disabled Timer interval: 300 seconds Interfaces that will be enabled at the next timeout:
Key Observations
- ❌ Err-disable recovery is disabled for
psecure-violation. - ⏳ The default recovery timer is
300 seconds(5 minutes).
To enable automatic recovery for port security violations, we must explicitly configure it.
Enabling Err-Disable Recovery
To enable Err-Disable Recovery for port security violations, use the following command:
SW1(config)# errdisable recovery cause psecure-violation
To adjust the recovery interval (default is 300 seconds), use:
SW1(config)# errdisable recovery interval 60
This sets the recovery timer to 60 seconds.
Verifying Err-Disable Recovery
SW1# show errdisable recovery ErrDisable Reason Timer Status ----------------- -------------- !!! Output omitted !!! psecure-violation Enabled !!! Output omitted !!! Timer interval: 60 seconds Interfaces that will be enabled at the next timeout: Interface Errdisable reason Time left(sec) --------- ----------------- -------------- Gi0/1 psecure-violation 48
- ✅ psecure-violation recovery is now enabled.
- ✅ The recovery timer is set to 60 seconds.
- ✅ Interface
Gi0/1will automatically recover in 48 seconds.
Automatic Recovery in Action
When the timer expires, the switch attempts to restore the err-disabled interface. The logs will show:
*Jan 21 11:22:46.892: %PM-4-ERR_RECOVER: Attempting to recover from psecure-violation err-disable state on Gi0/1 *Jan 21 11:22:48.918: %LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to up *Jan 21 11:22:49.918: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
✅ The interface is automatically re-enabled without requiring manual intervention.
Important Reminder: Disconnect Unauthorized Devices!
While Err-Disable Recovery is convenient, you must disconnect the unauthorized device before the timer expires. Here’s why:
1. If a secure MAC address is manually configured, the interface immediately enters err-disabled mode again when the unauthorized device sends traffic.
2. If the secure MAC address was dynamically learned, it is cleared when the interface enters err-disabled mode.
- If the unauthorized device is still connected when the port recovers, its MAC address may be learned as the new secure MAC, which compromises network security.
Recap
To recover an err-disabled interface, you have two options:
✔ Manual Recovery:
- Remove the unauthorized device.
- Use
shutdown→no shutdownto reset the port.
✔ Automatic Recovery:
- Enable Err-Disable Recovery for
psecure-violation. - Configure a recovery timer using
errdisable recovery interval <time>.
Next Steps
Now that we know how to recover an interface, let’s explore the different violation modes available in Port Security and how they impact network behavior.
5. Violation Modes
Port Security provides three violation modes that define how the switch reacts when an unauthorized device attempts to send data through a secured port.
Previously, we covered the default mode—Shutdown, which completely disables the port upon a security violation. Now, let’s explore all three violation modes in detail.
1️⃣ Shutdown Mode (Default)
The shutdown mode is the strictest and most secure violation mode.
- 🚫 Action: The switch disables the port, placing it in an err-disabled state.
- 🔔 Notification: A syslog and/or SNMP alert is generated when the violation occurs.
- ⛔ Traffic Handling: The port is completely shut down, and all traffic stops.
- 📊 Violation Count: The counter increments only once, when the port enters err-disabled state.
Note: Once the port is disabled, no additional logs are generated, even if the unauthorized device continues sending traffic.
This mode offers maximum security by immediately shutting down the compromised port. Manual intervention or Err-Disable Recovery is required to bring it back online.
2️⃣ Restrict Mode
Restrict mode is a more flexible option than shutdown mode.
- 🚫 Action: The switch drops unauthorized traffic, but the port remains active.
- 🔔 Notification: A syslog message and/or SNMP alert is generated each time an unauthorized MAC address is detected.
- ✅ Traffic Handling: Authorized devices remain unaffected and can continue to communicate.
- 📊 Violation Count: The counter increments every time an unauthorized MAC address sends a frame.
This mode balances security and availability, ensuring that unauthorized devices are blocked while allowing normal traffic for authorized users.
Violation Mode: Restrict Configuration
Let’s take a hands-on look at how Restrict Mode operates in practice!

Step 1: Enabling Port Security
First, enable Port Security on interface G0/1:
SW1(config)# int g0/1 SW1(config-if)# switchport port-security
Step 2: Manually Authorizing PC1’s MAC Address
This time, I will statically authorize PC1’s MAC address. Let’s explore the available port security options:
SW1(config)# int g0/1 SW1(config-if)# switchport port-security ? aging Port-security aging commands mac-address Secure mac address maximum Max secure addresses violation Security violation mode
Now, we configure PC1’s MAC address (AAAA.BBBB.CCCC) as the secure MAC address:
SW1(config-if)# switchport port-security mac-address AAAA.BBBB.CCCC
Step 3: Enabling Restrict Mode
Next, let’s configure the violation mode to Restrict:
SW1(config-if)# switchport port-security ? aging Port-security aging commands mac-address Secure mac address maximum Max secure addresses violation Security violation mode
The available violation modes are shown below:
SW1(config-if)# switchport port-security violation ? protect Security violation protect mode restrict Security violation restrict mode shutdown Security violation shutdown mode
To enable restrict mode:
SW1(config-if)# switchport port-security violation restrict
Step 4 :Verifying the Configuration
We can now check the status of Port Security on G0/1:
SW1# show port-security interface g0/1
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Restrict
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 1
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0000.0000.0000:0
Security Violation Count : 0
Here we can see:
- Port Status:
Secure-up, meaning the port is operational. - Violation Mode:
Restrict, confirming the configured mode. - Security Violation Count:
0, as no unauthorized traffic has been detected yet.
Step 5: Testing Restrict Mode
Now, let’s connect an unauthorized device to G0/1 and observe what happens.

When the unauthorized device sends data, the switch detects a security violation and logs it:
*Jan 21 13:52:10.469: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violatio n occurred, caused by MAC address DDDD.EEEE.FFFF on port GigabitEthernet0/1 . *Jan 21 13:52:21.138: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violatio n occurred, caused by MAC address DDDD.EEEE.FFFF on port GigabitEthernet0/1 . *Jan 21 13:52:26.601: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violatio n occurred, caused by MAC address DDDD.EEEE.FFFF on port GigabitEthernet0/1
Each log entry corresponds to a frame sent by the unauthorized device (DDDD.EEEE.FFFF).
Step 6: Checking Port Security Status Again
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Restrict£ Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 1 Sticky MAC Addresses : 0 Last Source Address:Vlan : DDDD.EEEE.FFFF:1 Security Violation Count : 9
Observations
✔ Port Status: Secure-up, meaning authorized devices can still use the port.
✔ Last Source Address: Displays the MAC address of the unauthorized device (DDDD.EEEE.FFFF).
✔ Security Violation Count: 9, meaning the switch has detected and logged nine unauthorized frames.
Restrict mode effectively blocks unauthorized traffic while keeping the port operational for authorized devices.
Violation Mode: Protect
The final violation mode, Protect, is the most lenient.
- 🚫 Action: Unauthorized traffic is silently discarded.
- ❌ Notification: No syslog or SNMP messages are generated.
- ✅ Traffic Handling: Authorized devices continue to use the port.
- ❌ Violation Count: The counter does not increase for unauthorized frames.
Unlike Restrict mode, Protect mode does not log violations, making it a good choice when security violations are expected but do not need monitoring.
Configuring Protect Mode
Let’s configure Protect mode in action!

Step 1: Enabling Port Security & Statically Setting PC1’s MAC Address
SW1(config)# int g0/1
SW1(config-if)# switchport port-security
SW1(config-if)# switchport port-security mac-address AAAA.BBBB.CCCC
Step 2: Setting Violation Mode to Protect
SW1(config-if)# switchport port-security violation protect
Testing Protect Mode
Now, an unauthorized device is connected to G0/1 and attempts to send traffic.

🚫 Results:
- The unauthorized device’s traffic is silently dropped.
- No syslog messages appear on SW1.
- The violation count does not increase.
Verifying Protect Mode Configuration
Let’s verify the configuration and port status:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up £Violation Mode : Protect Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 1 Sticky MAC Addresses : 0 Last Source Address:Vlan : DDDD.EEEE.FFFF:1 Security Violation Count : 0
Observations
✔ Port Status: The port is Secure-up and operational.
✔ Violation Mode: Displays Protect, confirming the configuration.
✔ Violation Count: Remains 0, as no violations are logged.
Protect mode silently prevents unauthorized access without logging violations or disabling the interface.
Key Takeaways for Protect Mode
- Protect mode only drops unauthorized traffic.
- No logs or violation counters are maintained.
- The port remains fully operational for authorized devices.
As the name suggests, protect mode focuses on protecting the port from unauthorized MAC addresses, without additional actions.
Summary of Violation Modes
Let’s recap the actions performed by each violation mode:
| Violation Mode | Drops Unauthorized Traffic | Generates Logs (Syslog/SNMP) | Puts Interface in Err-Disabled State |
|---|---|---|---|
| Shutdown (Default) | ✅ Yes | ✅ Yes (Once) | ✅ Yes |
| Restrict | ✅ Yes | ✅ Yes (For Each Violation) | ❌ No |
| Protect | ✅ Yes | ❌ No | ❌ No |
Take some time to remember about this !
6. Sticky Secure MAC Address
Let me introduce you to an advanced feature that can make port security easier to manage: Sticky Secure MAC Address learning.
This feature allows the switch to dynamically learn MAC addresses and automatically add them to the configuration, saving you from manually inputting each MAC address.
Enabling Sticky Secure MAC Address
To enable sticky learning, simply use the following commands on your interface:
SW1(config)# int g0/1 SW1(config-if)# switchport port-security SW1(config-if)# switchport port-security mac-address sticky
Once this is done, any device sending traffic through this port will have its MAC address learned dynamically as a secure MAC address.
Verifying Sticky Learning
Before the port receives any traffic, you’ll notice the sticky MAC address count is 0:
SW1# show port-security interface g0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 0 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0000.0000.0000:0 Security Violation Count : 0
Now, let’s say PC1 sends traffic through the switch.

The switch will dynamically learn its MAC address, and you can verify this:
SW1# show port-security interface g0/1
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address:Vlan : AAAA.BBBB.CCCC:1
Security Violation Count : 0
You see? The MAC address AAAA.BBBB.CCCC from PC1 is now learned and secured.
Checking the Running Configuration
You’ll also find that the sticky MAC address is automatically added to the running configuration:
SW1# show run int g0/1
interface GigabitEthernet0/1
switchport mode access
switchport port-security mac-address sticky
switchport port-security mac-address sticky AAAA.BBBB.CCCC
switchport port-security
Sticky MAC addresses are only saved in the running configuration. If you restart the switch without saving, the configuration will be lost. Make sure to save your configuration using:
SW1# copy running-config startup-config
Why Use Sticky Secure MAC Address?
Sticky learning is perfect when you don’t want to manually configure MAC addresses but still need to secure your ports. It automatically learns and secures devices, and once you save the configuration, it becomes as solid as a manually configured static MAC address.
7. Conclusion
Now that you’ve learned all about Port Security, let’s summarize the key points !
Key Takeaways
- What is Port Security?
- Port Security is a feature used to control and restrict access to switch interfaces based on source MAC addresses. It helps prevent unauthorized devices from connecting to your network.
- Port Security is a feature used to control and restrict access to switch interfaces based on source MAC addresses. It helps prevent unauthorized devices from connecting to your network.
- MAC Address Learning
- Switches can learn MAC addresses dynamically or be configured manually.
- You can limit the number of allowed MAC addresses per port for added security.
- Violation Modes
- Shutdown: Disables the port entirely (default mode).
- Restrict: Blocks unauthorized traffic while keeping the port operational and logging violations.
- Protect: Silently drops unauthorized traffic without generating logs or disabling the port.
- Each mode has its specific use case, and knowing when to use them is crucial.
- Recovering Interfaces
- Manual Recovery: Use
shutdownandno shutdowncommands to reset the interface. - Err-Disable Recovery: Automatically re-enables the port after a timeout period. This is particularly useful in larger networks.
- Manual Recovery: Use
- Sticky MAC Addresses
- Sticky learning dynamically secures MAC addresses and adds them to the running configuration.
- Remember to save the configuration (
copy running-config startup-config) to make the changes permanent.
For more information : https://www.cisco.com/en/US/docs/general/Test/dwerblo/broken_guide/port_sec.html
