RADIUS
1. What is RADIUS?
RADIUS stands for Remote Authentication Dial-In User Service. It’s a AAA protocol (Authentication, Authorization, and Accounting) created by the Internet Engineering Task Force (IETF). RADIUS is widely used to manage secure access to network devices across many platforms and vendors.
Purpose of RADIUS
RADIUS helps organizations secure their networks by verifying the identity of users trying to log in. It centralizes access control, making it easier to manage who can use the network and what they can do.
How RADIUS Works
RADIUS uses a client-server model:
- RADIUS Client: The device (like a router or switch) where users try to log in. It sends their credentials to the RADIUS server.
- RADIUS Server: The system that checks these credentials and decides whether to accept or reject the user.
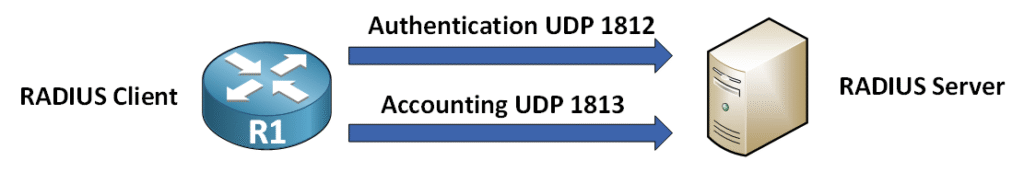
RADIUS communicates using UDP as its transport protocol, with:
- Default Authentication Port: 1812
- Default Accounting Port: 1813
Older ports (1645 for authentication and 1646 for accounting) are sometimes used with older systems, but most modern setups use ports 1812 and 1813.
Important Note: Only passwords are encrypted during transmission with RADIUS. Other data, like usernames and session details, are sent in plain text, which can be risky if the data is intercepted. For highly secure networks, protocols like TACACS+ are often preferred because they encrypt all data.
2. RADIUS Authentication Process
Combined Authentication and Authorization
With RADIUS, authentication (checking who the user is) and authorization (deciding what the user can do) happen at the same time. Once a user logs in, the RADIUS server verifies their credentials and sends back access permissions in a single step.
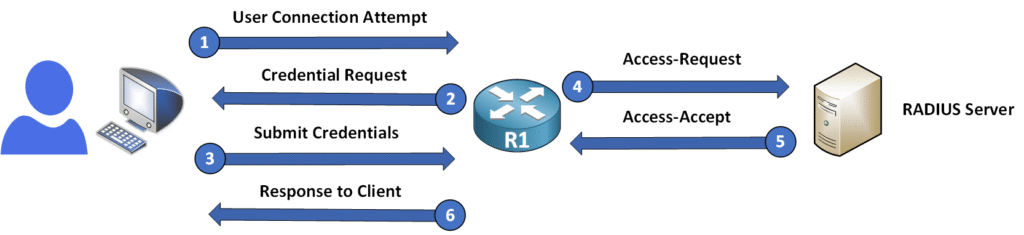
Authentication Workflow
Here’s how the RADIUS authentication process works:
- Access-Request: The RADIUS client (e.g., router) sends the user’s credentials to the RADIUS server.
- Access-Accept/Reject: The server checks the credentials. If they’re correct, it approves the login (Access-Accept). If not, it denies access (Access-Reject).
- Access-Challenge: In some cases, the server may ask for additional verification, like a second password or security question, before allowing access.
3. RADIUS Authorization and Accounting
Authorization
Upon authentication, the RADIUS server includes access permissions in its response. However, RADIUS doesn’t allow detailed control over individual commands that users can run. It only supports user-level access permissions, which limits detailed control over individual commands.
Accounting
RADIUS also keeps track of what users do on the network through accounting logs.
- What It Tracks:
- When users log in and log out
- How long they’re connected
- How much data they use
Note: RADIUS does not log specific commands entered by users, so it’s less useful for detailed auditing compared to other protocols like TACACS+.
4. RADIUS Configuration
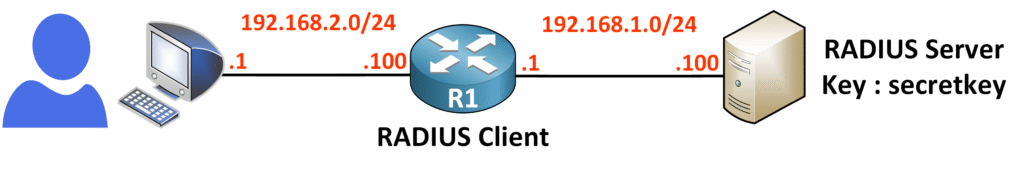
Setting up RADIUS with AAA involves enabling the AAA framework, defining the RADIUS server, and applying authentication settings. Below are the steps to configure RADIUS on a device with the server 192.168.1.100 and the shared key secretkey.
Enable AAA
Activate the AAA framework on the device with the following command:
R1(config)# aaa new-model
This command enables the “new model” of AAA, allowing centralized control for authentication, authorization, and accounting.
Configure the RADIUS Server
Specify the RADIUS server’s IP address and the shared key for secure communication:
R1(config)# radius-server host 192.168.1.100 key secretkey
radius-server host: Defines the RADIUS server’s IP address.key: Sets the shared password for secure communication between the network device and the RADIUS server.
By default, RADIUS uses:
- Port 1812 for authentication
- Port 1813 for accounting
If you want to specify custom ports, you can use:
R1(config)# radius-server host 192.168.1.100 auth-port 1812 acct-port 1813 key secretkey
Define Authentication Method
Set up the authentication method so that RADIUS is the primary method, and the local database is used as a backup if the RADIUS server is unavailable:
R1(config)# aaa authentication login default group radius local
Explanation of the command:
aaa authentication login: Configures authentication for login sessions.default: Applies the configuration to all login methods (e.g., console, VTY lines).group radius local: Uses RADIUS first. If the server doesn’t respond, the local user database acts as a fallback.
Create Local User Accounts
For fallback authentication, create a local user account with an encrypted password:
R1(config)# username Admin secret pingmynetw0rk!
This ensures that if the RADIUS server is unreachable, the local user Admin can still log in.
Apply Authentication to Specific Lines
To apply the AAA authentication to specific lines, such as VTY (used for Telnet or SSH), use the following commands:
R1(config)# line vty 0 4 R1(config-line)# login authentication default
This ensures that all login attempts on VTY lines follow the authentication method defined in Step 3.
Summary of Configuration
Here’s a complete example of the configuration:
R1(config)# username Admin secret pingmynetw0rk! R1(config)# aaa new-model R1(config)# radius-server host 192.168.1.100 key secretkey R1(config)# aaa authentication login default group radius local R1(config)# line vty 0 4 R1(config-line)# login authentication default
Key Notes
- Fallback Authentication: Always include the local database as a backup method in case the RADIUS server becomes unreachable.
- Security: Use encrypted passwords with the
secretkeyword instead of plain text passwords. - Custom Lines: If you need different authentication rules for specific lines (e.g., console vs. VTY), define custom method lists instead of using
default.
5. Benefits and Limitations of RADIUS
Benefits
RADIUS has several advantages:
- Widely Supported: It works with devices from many vendors, making it great for mixed environments.
- Lightweight and Efficient: It’s fast and works well for small to medium-sized networks.
Limitations
Despite its advantages, RADIUS has some downsides:
- Limited Security: Only passwords are encrypted, while other data is sent in plain text. This makes it less secure for sensitive environments.
- No Command Tracking: RADIUS doesn’t record specific commands that users run, which limits its ability to provide detailed activity logs.
- Single Privilege Level: RADIUS supports only one permission level for users, so it can’t control which specific commands each user can use.
Next Steps: In the next lesson, we’ll dive into TACACS+, another AAA protocol. We’ll explore how it works, its differences from RADIUS, and why it’s often used in high-security environments.
