TACACS+
1. What is TACACS+?
TACACS+ (Terminal Access Controller Access-Control System Plus) is an AAA protocol created by Cisco. It helps manage secure access to network devices like routers, switches, and firewalls. While it was initially proprietary, TACACS+ is now widely supported by other vendors, making it a great choice for complex networks.
Purpose of TACACS+
TACACS+ is designed for detailed access control. Unlike other protocols, it separates the three AAA functions—authentication, authorization, and accounting—to give administrators more control over user access, actions, and logs.
How TACACS+ Works
TACACS+ uses a client-server model with TCP on port 49 to ensure reliable and secure communication. Here’s how it works:
- TACACS+ Client: The network device (e.g., a router or switch) sends user login details to the TACACS+ server for verification.
- TACACS+ Server: This is the central system that verifies user credentials, checks permissions, and logs all user actions.
Unlike RADIUS, TACACS+ encrypts all the data sent between the client and server, making it more secure for sensitive networks.

2. TACACS+ Authentication Process
In TACACS+, the authentication process is fully encrypted, which protects all user details during transmission.
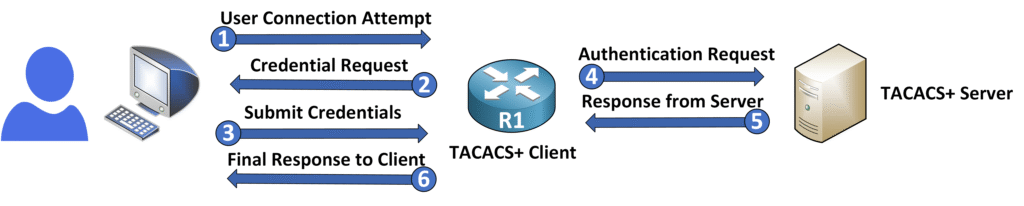
Authentication Workflow
Here’s how TACACS+ authenticates a user:
- Authentication Request: The network device (client) sends the user’s login details to the TACACS+ server.
- Server Response: The server checks the credentials and replies with either:
- Accept: The user is granted access.
- Reject: Access is denied if the credentials are incorrect.
This encryption ensures no sensitive data is exposed, even if someone intercepts the communication.
3. TACACS+ Authorization and Accounting
Authorization
TACACS+ provides granular control over user actions:
- Command-Level Authorization: Every command a user tries to execute is checked against their permissions.
- Example: A user might be allowed to run
show runto view the configuration but not useconfigure terminalto make changes.
This ensures users can only perform tasks they are authorized for, improving both security and accountability.
Accounting
TACACS+ keeps detailed logs of all user actions:
- Command Logging: Every command a user executes is recorded.
- Session Details: Tracks when users log in, log out, and the results of their actions.
Why It’s Useful: These logs create a full audit trail, making it easier to troubleshoot issues or review compliance.
4. TACACS+ Configuration Steps
Setting up TACACS+ on a Cisco device involves defining the TACACS+ server, enabling AAA, and applying the configuration to user authentication. Here’s a step-by-step guide:

Enable AAA
Before configuring TACACS+, you need to enable the AAA framework on the device:
R1(config)# aaa new-model
This command activates AAA, allowing you to manage authentication, authorization, and accounting centrally.
Define the TACACS+ Server
Next, specify the TACACS+ server’s IP address and the shared encryption key:
R1(config)# tacacs-server host 192.168.1.100 key tacacskey
tacacs-server host: Defines the IP address of the TACACS+ server.key: Sets the shared key for secure communication between the network device and the TACACS+ server.
Configure Authentication
Set up authentication so that TACACS+ is the primary method, with a fallback to the local database:
R1(config)# aaa authentication login default group tacacs+ local
Explanation:
aaa authentication login: Configures login authentication settings.default: Applies the authentication rule to all login methods (e.g., console, VTY lines).group tacacs+ local: Uses TACACS+ first. If the server is unavailable, the local database is used as a backup.
Apply Authentication to User Access Lines
To enforce TACACS+ authentication for specific access lines like VTY (Telnet or SSH), link the authentication configuration to these lines:
R1(config)# line vty 0 4 R1(config-line)# login authentication default
This ensures that all VTY lines use the authentication rules configured in Step 3.
Create Local User Accounts
To ensure fallback authentication works when the TACACS+ server is unavailable, create a local user account with an encrypted password:
R1(config)# username Admin secret pingmynetw0rk!
This provides a backup method for logging in if the TACACS+ server cannot be reached.
Complete Configuration
Here’s the full configuration example for TACACS+ on device R1:
R1(config)# aaa new-model R1(config)# tacacs-server host 192.168.1.100 key tacacskey R1(config)# aaa authentication login default group tacacs+ local R1(config)# username Admin secret pingmynetw0rk! R1(config)# line vty 0 4 R1(config-line)# login authentication default
With this configuration, TACACS+ will handle login authentication as the primary method, with a secure fallback to the local user database.
5. Benefits and Limitations of TACACS+
Benefits
TACACS+ is ideal for high-security environments due to its advanced features:
- Granular Control: Allows specific command-level permissions.
- Enhanced Security: Encrypts the entire communication, including usernames, passwords, and session data.
- Detailed Logs: Tracks every user action, making audits and compliance checks easier.
Limitations
Despite its benefits, TACACS+ has a few drawbacks:
- More Resources Needed: It uses more system resources compared to RADIUS.
- Complex Setup: Configuration is more detailed, which might be challenging for smaller teams.
