Wireless vs Wired Networks
1. How Data is Transmitted in Wired and Wireless Networks
Let’s start with a question: how does data travel from one device to another?
🔍 In Wired Networks with a Switch
In wired networks with a switch, data travels directly to the recipient:

When PC1 sends data to PC3, the switch forwards the data only to PC3 based on its MAC address.

- PC2 and PC4 don’t receive the data because the switch sends it privately to the intended recipient.
- Communication occurs in full-duplex mode—PC1 and PC3 can send and receive data simultaneously without collisions.
🔍 In Hub-Based Wired Networks
In hub-based wired networks, data is sent as a broadcast:
- When PC1 sends data to PC3, the hub broadcasts the data to all devices on the network (PC2, PC3, and PC4).
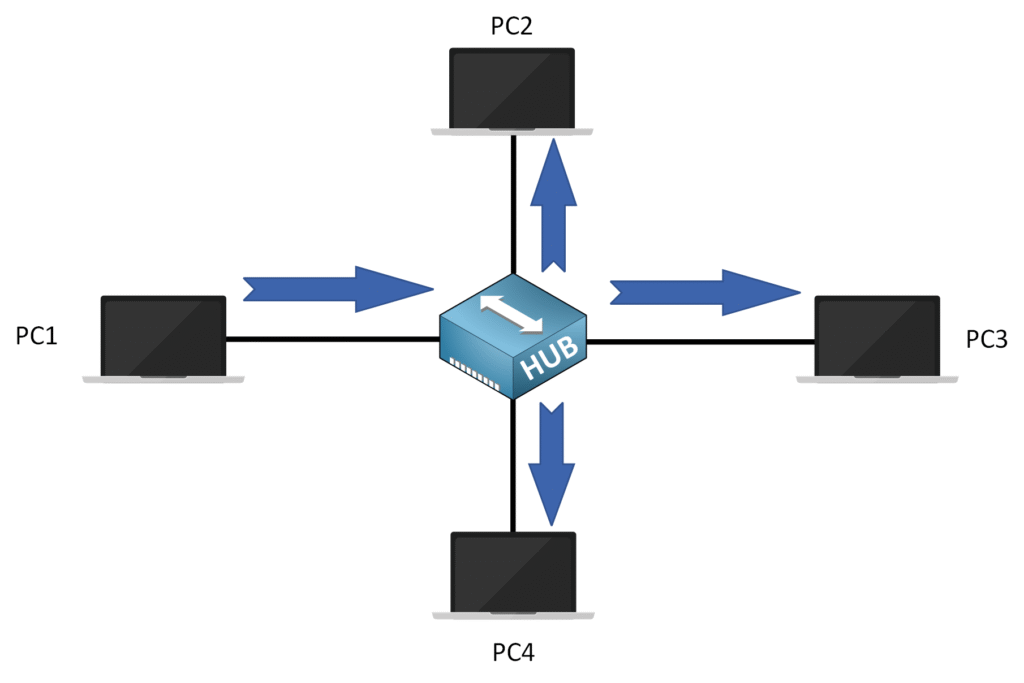
- PC3 is the only device that processes the data while PC2 and PC4 ignore it.
- Communication is in half-duplex mode when using a hub, meaning devices can only send or receive data, not both at the same time.
⚠️ This broadcast behavior often leads to collisions when multiple devices, like PC1 and PC4, try to send data at the same time.
🔍 In Wireless Networks with an Access Point (AP)
In wireless networks with an Access Point (AP), data behaves similarly to a hub:
When PC1 sends data to PC3, the AP broadcasts the data to all devices within range.

- PC3 processes the data, while other nearby devices ignore it.
- Communication is in half-duplex mode, so devices must wait their turn to send or receive data.
⚠️ Since the data is broadcast through the air, encryption is necessary to protect it from being intercepted.
✅ With a switch, data is sent only to the correct recipient. In contrast, hubs and wireless APs broadcast the data, making it accessible to all devices in range, increasing the risk of collisions and privacy concerns.
2. Challenges of Wireless Networks
🔍 Broadcast-like Behavior
In wireless networks, all devices within range can “hear” the data being transmitted, similar to devices connected to a hub. This makes wireless communication more susceptible to data interception and privacy issues.
⚠️ In wired networks, data sent over the LAN isn’t usually encrypted—it’s assumed to be private within the network. However, in wireless networks, encryption is critical, even within the LAN, to prevent unauthorized access. Without encryption, anyone within range could intercept your data.
💬 We will cover the security of data in wireless networks later in the course.
Collisions and Half-Duplex Communication
Since wireless networks operate in half-duplex mode, devices can’t send and receive data simultaneously. If two devices try to send data at the same time, collisions occur, causing data loss.
✅ So, how do devices send traffic without collisions in wireless networks?
3. CSMA/CA: Avoiding Collisions
Wireless LANs (WLANs) use:
- Half-duplex: Only one device can send or receive data at a time.
- Shared media: All devices use the same radio channel to communicate.
⚠️ The main challenge with wireless communication is that devices cannot detect a collision while sending data because they cannot listen and transmit simultaneously.
Instead of detecting collisions after they occur, CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) aims to prevent collisions from happening in the first place by coordinating when devices send data.
🔍 How CSMA/CA Works

- Channel Check: The client listens to the channel to check if it’s free (no other traffic detected).
- Random Wait if Busy: If the channel is busy, the client waits for a random period before checking again.
- Frame Transmission: If the channel is free, the client transmits the frame.
- Acknowledgment (ACK): Every transmission must be acknowledged. If the wireless client doesn’t receive an acknowledgment, it interprets this as a failed transmission due to a possible collision and initiates the process again.
🔍 RTS/CTS Mechanism (Optional)
The RTS/CTS mechanism is an optional feature used to prevent frame collisions caused by the hidden node problem. Here’s how it works:
- Request to Send (RTS): The client sends an RTS packet to the AP, requesting permission to transmit data.
- Clear to Send (CTS): The AP responds with a CTS packet to grant permission to use the channel.
- Once the CTS is received, the client sends the frame.
- The ACK confirms successful reception of the data.
💡 Think of It Like This: It’s like waiting your turn to speak in a conversation—you check if someone else is speaking before you start. If you don’t get a signal that it’s your turn, you wait before trying again.
📢 The RTS/CTS process adds coordination to reduce collisions in networks with hidden nodes but is not required in all wireless setups. While this level of detail isn’t mandatory for the CCNA exam, it helps to understand how CSMA/CA can go deeper to handle specific network scenarios.
4. Conclusion
Now that we’ve covered how data is transmitted in wired and wireless networks, the challenges wireless networks face, and how CSMA/CA helps prevent collisions, you’re better equipped to understand the mechanics behind network communication.
📢 In the next section, we’ll dive deeper into Wireless LAN 802.11 Service Sets to explore how wireless networks organize devices. Let’s continue!
